Resilient Access - The secure access layer for all your data
Resilient Access™
Resilient Access is a distributed policy evaluation engine for authentication and authorization of user access. Dynamic policies, appropriate for the contexts in which they are applied, protect applications and data, and are evaluated using a trusted set of authoritative sources.
The Resilient environment is comprised of several classes of networked components: Applications (functioning as Relying Parties), the Resilient Platform centered on the Policy Workflow Engine (PWE) and managed through the Administrative Console (AC), and authoritative information sources (Authorities) that are orchestrated by the PWE.
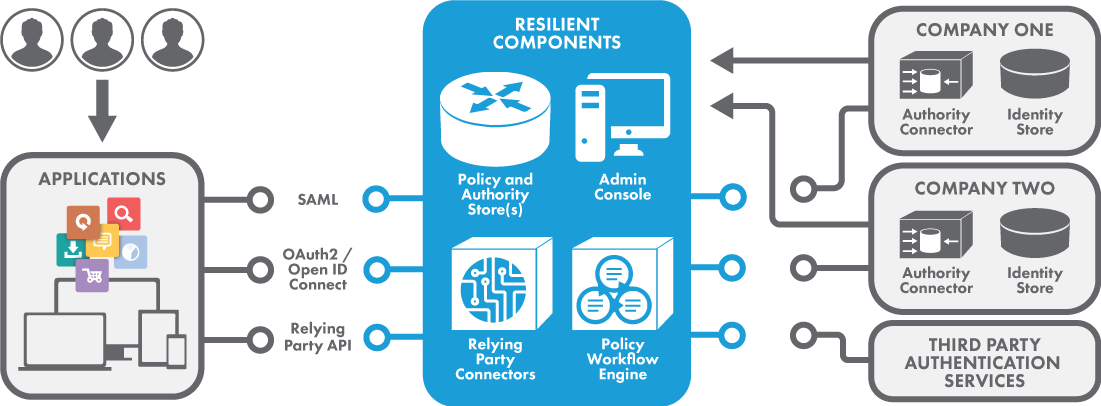
Applications:
Applications connect to the Resilient Platform utilizing Resilient-provided Relying Party connectors that interface the applications and manage the policies by which they are to be protected. Policies are evaluated when required by the Applications (such as on initial access) and are conveyed to Resilient Platform through the PWE using application-appropriate interfaces (e.g., SAML, OAuth, etc.) The Application becomes a Relying Party upon the rest of the system, which in aggregate functions as a PDP for the policy.
Resilient Platform:
The Resilient Platform is a distributed system of components centered upon the PWE, but also consisting of a variety of administrative and meta-data authorities that support and manage the relationships between the parties participating in the network. On receiving a policy to be evaluated, the PWE structures it into a series of exchanges among the suitable Authorities. On completion, the PWE will notify the application whether the policy has been satisfied along with returning policy-defined attribute information for further use by the Application. The Administrative Console provides organizations with the access to compose and manage their policies and to configure and connect their Authorities and Relying Parties. Other Platform components provide privacy-enhancing services, allowing individual datum or aggregations to be named and policy-protected while being referenced and utilized in the Resilient environment but without disclosing their actual content, except for accessors who satisfy the policy protecting them.
Authorities:
The distributed set of Authorities enables policies to use in situ information resources appropriate to participating organizations. This simplifies construction of the environment by eliminating additional enrollment operations and their administrative burdens. Resilient provides Authority Connectors to interface Authorities to the environment, using the access protocols appropriate for the Authority.
-
Up and running in days
-
Easily integrates with your existing cyber and identity management solutions
-
Network-based architecture easily scales with your needs
-
Standards-based and custom RESTful APIs for connecting authoritative sources and applications
-
Bi-directional policy enforcement
-
A graphical UI for defining and managing policies based on a set of connected authorities
-
A distributed workflow technology to resolve policy conditions
-
Support for identity and access management standards (SAML, OAuth, XACML, Etc.)

